Welcome to an in-depth exploration of our cutting-edge remote monitoring system, meticulously crafted
to
meet the stringent security requirements of today's technical landscape. On this page, we delve into the
core
components and security architecture of our system, focusing particularly on the implementation of a Virtual
Private Network (VPN) and Two-Factor Authentication (TFA). At Got Monitoring, we prioritize security at
every
level of our system design, and our commitment to safeguarding your critical infrastructure is evident in
our
comprehensive approach to security. Join us as we uncover how our system is built with security in mind,
offering unparalleled protection for your remote monitoring needs.
Our approach to securing the remote monitoring system begins with the implementation of a Virtual
Private
Network (VPN). With Got Monitoring, we ensure the comprehensive security of the entire system through the
integration of VPN technology and Two-Factor Authentication (TFA). We meticulously set up our customers with
a
VPN client, configuring it to first authenticate users with their correct username and password. Upon
successful
authentication, our system seamlessly integrates with authentication apps providing users with verification
codes for an additional layer of security. We support reputable authentication methods available in the
market.
Once the verification process is completed, users are granted access to the VPN network. This access
is
managed and tailored to each customer's profile, ensuring that they only have access to the resources and
systems pertinent to their operational requirements. We facilitate this setup by utilizing the 2D codes
provided
by the VPN system, which are uniquely assigned to each customer. Our VPN infrastructure is meticulously
designed
to meet industrial standards, prioritizing security in its architecture and operations.
In practical terms, our VPN implementation establishes secure communication channels between remote
sites
and the central monitoring system. Utilizing industry-standard encryption protocols such as OpenVPN or
IPsec, we
encrypt data end-to-end, safeguarding it from unauthorized access and ensuring the confidentiality of
sensitive
information. By establishing secure tunnels, our VPN infrastructure protects against interception or
tampering
by malicious actors, thereby preserving the integrity of data exchanged over the network.
This robust combination of Virtual Private Network (VPN) technology and Two-Factor Authentication
(TFA)
reflects our commitment to ensuring the utmost security of the remote monitoring system. By leveraging these
advanced security measures, we provide our customers with a comprehensive solution that protects their
critical
infrastructure and data from threats and vulnerabilities.
Once a customer is logged in, we implement a sophisticated group-based access control mechanism to
further
enhance security. Depending on the customer's requirements, we create dedicated VPN groups tailored to their
specific equipment and control systems deployed at their job sites. These VPN groups ensure that each
customer's
equipment is isolated and accessible only to authorized personnel within their organization.
The Supervisory Control and Data Acquisition (SCADA) system, an integral component of our remote
monitoring solution, utilizes computers, networked data communications, and graphical user interfaces for
high-level process supervisory management. The SCADA system is accessible exclusively through the VPN
network.
It plays a critical role in overseeing and controlling industrial processes remotely. To ensure secure
access,
the SCADA system does not support HTTP or HTTPS connections from outside the VPN network. Instead, we deploy
website certificates on user computers to establish secure connections, safeguarding against unauthorized
access
and data breaches.
Access to the SCADA system is managed through usernames and passwords, with multiple levels of
security
implemented to differentiate between regular users and administrators. Administrators have elevated
privileges,
allowing them to configure access control settings, manage users, and monitor system performance.
Additionally,
the SCADA system offers advanced features such as user-specific access restrictions, real-time trend
analysis,
alarm notifications, and event escalation protocols.
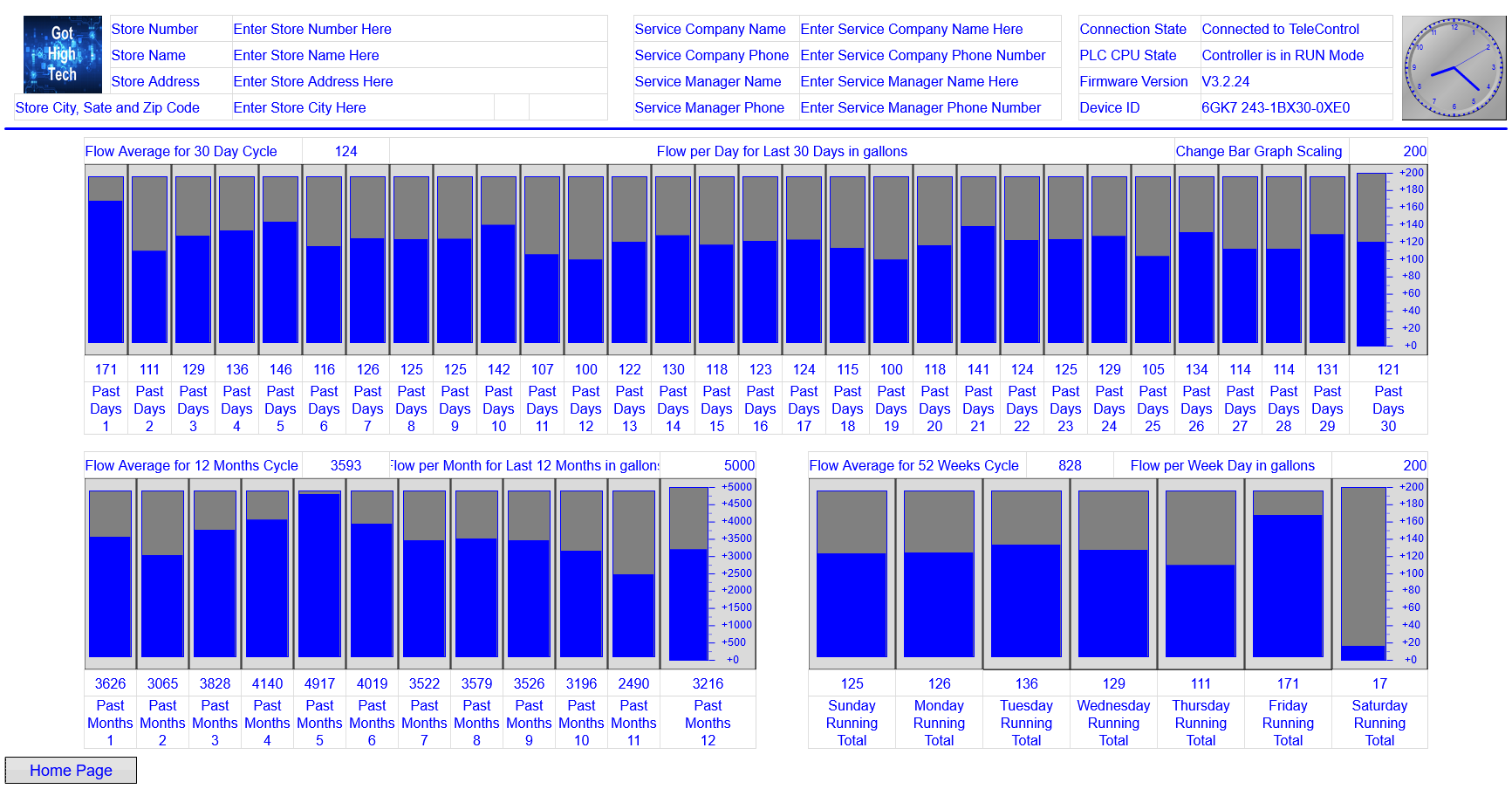
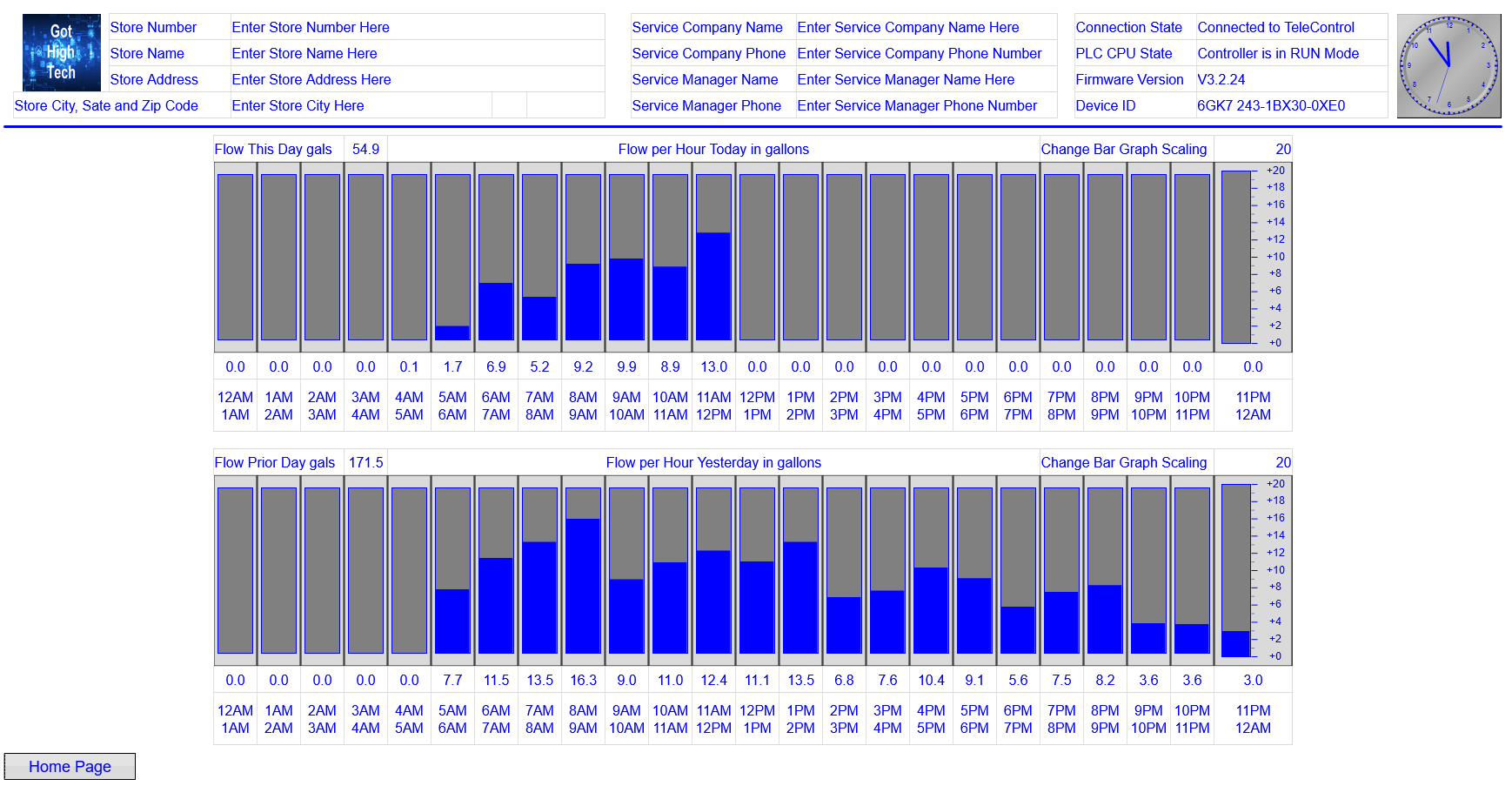
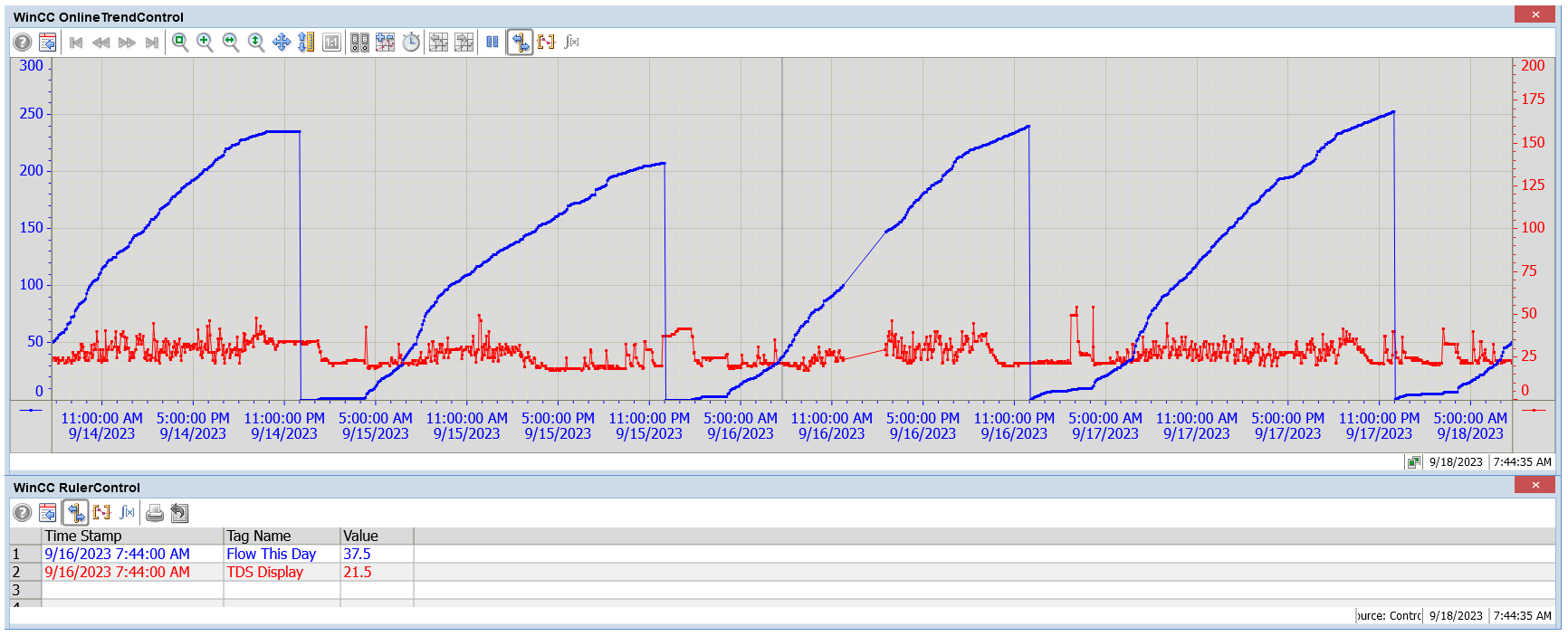
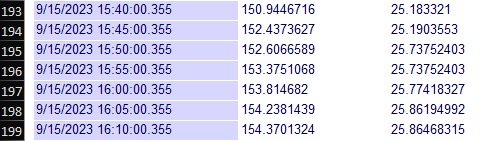
A standout feature of our SCADA system is its ability to conduct comprehensive trend analysis,
enabling
data-driven decisions by visualizing patterns and trends over time, contributing to enhanced system
optimization
and performance. Real-time alerts are a key aspect, providing timely notifications that facilitate proactive
maintenance, ensuring optimal system performance and upholding water quality standards.
Our SCADA system goes beyond reactive measures, incorporating preventive maintenance with event
triggers.
This innovative feature allows for efficient resource planning, providing advanced notice for service needs
and
preventing unexpected disruptions. Furthermore, the system enables historical analysis and optimization,
allowing you to track service intervals for proactive maintenance, contributing to the longevity and
reliability
of your system.
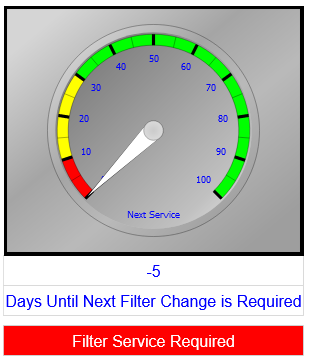
The system empowers you to configure notification thresholds for process values, providing the
flexibility
to customize alerts based on your unique requirements. This adaptability ensures your team receives timely
and
relevant information, facilitating prompt decision-making. Real-time process monitoring is a core feature,
offering a comprehensive view of your operations as they unfold. This real-time insight is complemented by
alarm
level thresholds through an alarm manager and secure email and/or text alerts, ensuring you stay informed
about
critical events promptly.
In the event of critical alarms or system events, the SCADA system automatically sends email and/or
text
message notifications to designated personnel. To ensure timely response and resolution, the system
incorporates
escalation levels, wherein unresolved alarms are escalated to the next available personnel if acknowledgment
is
not received within a specified timeframe.
Our robust reporting system ensures operational efficiency and regulatory compliance. Reports are
generated on a predefined schedule or triggered by specific events, such as tank overflow incidents. These
reports are securely stored on the report generator server and then transmitted to a network drive (NAS) via
the
VPN. Each customer accesses their reports through a secure user interface, using a unique username and
password.
To prevent data loss, automated backups are performed daily at 3 AM, ensuring redundancy and
availability.
These automated reports, generated at daily, monthly, and customizable intervals, provide timely
insights
into system performance. Stored securely and easily accessible, they guarantee transparency and reliability.
Supported by RAID technology, which mirrors data across two drives for redundancy and fault tolerance, our
system ensures data integrity and performance optimization. By consolidating multiple physical disk drives
into
a single logical unit, RAID enhances both data security and operational efficiency.
The NAS systems are strategically located in two geographically diverse locations, namely South Orange
County and Los Angeles, California, to ensure data redundancy and disaster recovery capabilities. Both NAS
systems are equipped with uninterruptible power supply (UPS) systems to mitigate the impact of power outages
and
ensure continuous operation.
Additionally, the Report Generator provides customers with a user-friendly web interface for creating
and
customizing their own reports. This feature empowers users to extract valuable insights from their data and
facilitates informed decision-making.
By implementing these comprehensive security measures and operational protocols, we ensure the
integrity,
confidentiality, and availability of critical infrastructure and data, thereby providing our customers with
a
secure and reliable remote monitoring solution.
Our remote monitoring system incorporates a robust solution, which revolutionizes the traditional data
transfer paradigm by adopting a pushing system. This innovative approach enables devices at remote sites to
autonomously transmit data to the SCADA system based on predefined conditions, ensuring efficient
utilization of
network resources. For instance, data transmission is triggered only when there is a significant 3% change
in
the device's status, minimizing unnecessary data transfer and optimizing network bandwidth.
A key feature is its integrated buffering system, which plays a crucial role in maintaining data
integrity
and resilience in the face of communication disruptions. In the event of a loss of communication between the
remote device and the SCADA system, data is securely stored locally on the device. This ensures that
critical
information is not lost during network outages or disruptions. Once communication is reestablished, the
buffered
data is automatically transmitted to the SCADA server, seamlessly synchronizing the remote device with the
central monitoring system.
In conclusion, in today's fast-paced business world, ensuring consistent water quality across multiple
locations is paramount. Here at Got Monitoring, we bring over three decades of engineering expertise to the
forefront, offering an advanced central control and monitoring system that delivers real-time insights
regardless of your location. Our system's robust communication network seamlessly integrates public and
private
networks, including mobile wireless and the Internet, ensuring comprehensive oversight of your water
systems.
With cutting-edge technology at your fingertips, managing and supervising machinery, accessing data reports,
and
receiving notifications becomes effortless. Our scalable platform is tailored to your specific requirements,
providing customized solutions throughout the system's lifecycle. Experience the simplicity of mastering
data
with our control and monitoring system, empowering you to make informed decisions and enhance operational
efficiency. More than just a company, we are pioneers of innovation, collaborating with businesses of all
sizes
to redefine possibilities in your industry. Ready to optimize your water management? Contact us today to
discover how our solutions can revolutionize your operations. We eagerly anticipate the opportunity to
discuss
your unique needs and embark on this journey together.